

 Dive into this edition of ‘The SOC case files’ to see how the Barracuda’s Managed XDR team recently contained a suspected ransomware attack after the attackers gained access to a company’s network before it installed Managed XDR, compromising several Windows machines and an administrator account. By the time the attackers returned to complete the attack, a suite of Barracuda Managed XDR solutions was in place — able to track, contain and neutralize the attack.
Dive into this edition of ‘The SOC case files’ to see how the Barracuda’s Managed XDR team recently contained a suspected ransomware attack after the attackers gained access to a company’s network before it installed Managed XDR, compromising several Windows machines and an administrator account. By the time the attackers returned to complete the attack, a suite of Barracuda Managed XDR solutions was in place — able to track, contain and neutralize the attack.
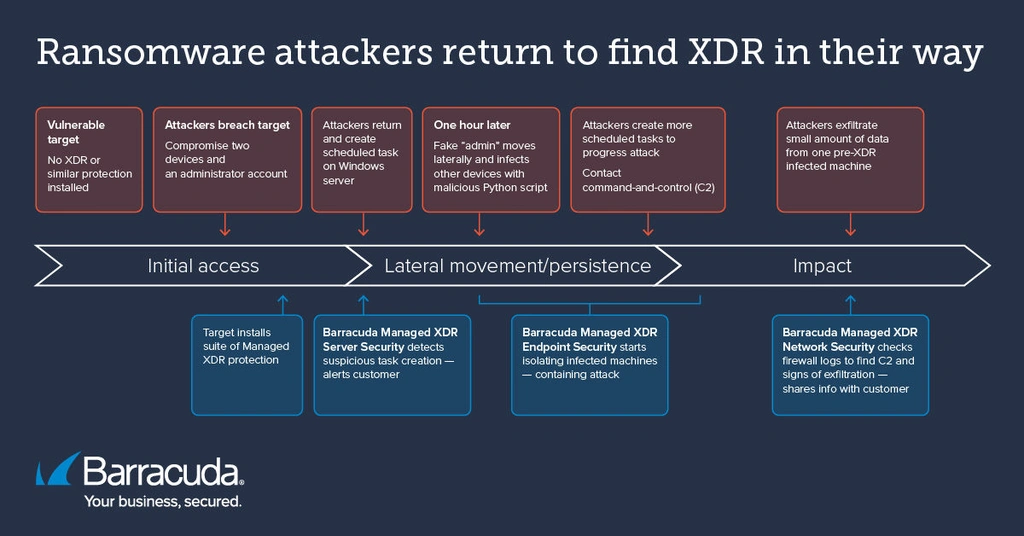
Incident summary
- At some point before the deployment of Barracuda Managed XDR, a suspected ransomware gang gained access to the vulnerable company’s network and compromised two machines and an administrator account.
- By the time the attackers tried to launch the main attack, however, a suite of Managed XDR solutions was in place, able to detect, monitor, contain and neutralize attack activity despite the preexisting breach.
- The attackers were unable to spread widely and cause significant damage, even as they created scheduled tasks, moved laterally, infected further machines with a Python-based malicious payload, contacted command-and-control (C2) and exfiltrated a small amount of data from one infected machine.
- The combined power of Managed XDR Server Security, Endpoint Security and Network Security isolated infected machines and shared insight from firewall logs that revealed the C2 communications and exfiltration, so that the customer was fully aware of what had happened and could anticipate potential fall out, address gaps and harden protection for the future.
How the attack unfolded
At 8:33 a.m., Barracuda’s SOC spotted the creation of a suspicious scheduled task in a Managed XDR customer’s network. The team immediately alerted the customer. It turned out to be an unfolding ransomware attack that had in fact started some time before the company installed Barracuda Managed XDR.
The ransomware gang had managed to gain access to the network, compromising two machines, including a Windows server and an account with administrative privileges.
However, by the time the attackers returned to launch the main attack, the victim had deployed a suite of Barracuda Managed XDR services, including Managed XDR Endpoint Security, Server Security and Network Security. Between them, these services were able to track and contain the unfolding incident.
The main attack
An hour after creating the suspicious scheduled task, the “administrator” had moved through the network to infect another three devices with a zipped Python file called python3.12.zip, which was then unzipped via PowerShell.
They also created additional scheduled tasks with random names such as \Task_e8ixq., T\Task_258bd060, \Task_f6isq and \Task_e8ixq.
The hijacked machines occasionally pinged their command-and-control (C2) server.
The cybersecurity analysts detected this activity and quarantined the machines to prevent them from interacting further with the network and spreading the attack.
The team also identified the file hashes of the malicious code and added them to the blocklist. This allowed the SOC to quarantine any other instances of the files within the environment.
Using firewall logs collected through Managed XDR Network Security, the SOC team was able to find evidence of the C2 communications with three of the five infected devices. They also discovered signs of data exfiltration, with a small amount of data sent to an external destination from one of the compromised machines.
On behalf of the customer, the SOC team tried to leverage SOAR (Security Automation and Response) and Automated Threat Response (ATR) to block the malicious IP address associated with the C2 server. However, a misconfiguration meant the attempted blocking wasn’t successful. The SOC instead worked with the customer to quickly add the blocklist directly on their firewall.
With Managed XDR in place, the attackers were prevented from doing any real damage.
Lessons learned
Despite the earlier breach that provided the attackers with access to the network, the suite of Managed XDR services deployed by the target meant that the attack activity was detected, tracked and blocked.
Barracuda Managed XDR Server Security detected the suspicious scheduled tasks created on the server, and the SOC used Managed XDR Endpoint Security to trace these events to different endpoints. Additionally, Managed XDR Network Security enabled the SOC team to identify communications with the malicious C2’s IP address.
Working together, the services provided the previously compromised victim with comprehensive protection that drastically reduced intruder dwell time, damage and disruption.
Visit the website for more information on Barracuda Managed XDR and SOC. For the latest on new features and upgrades and new detections for Barracuda Managed XDR, check out the most recent release notes.
Why scheduled tasks can be a security red flag
The first security alert in this incident was triggered by the creation of a suspicious scheduled task. Ransomware attackers often use scheduled tasks to automate different stages of the attack, maximizing the impact of the attack while reducing the chances of detection.
Attackers create scheduled tasks for several reasons, including:
- To release the ransomware payload at a specific time
- To maintain access to the network, for example, by scheduling tasks to rerun malware at intervals, even if it is detected and removed
- To help with stealthy data exfiltration, for example, by collecting and removing information at intervals
- To turn off antivirus software, firewall protections, or system recovery tools, making it harder for the security team to remediate or recover from the incident
- To distribute ransomware to connected devices across the network
- To delete traces of attack activity after encryption, making it harder for security teams to investigate how the attack unfolded
Barracuda Managed XDR is an extended visibility, detection and response (XDR) service underpinned by an expert security operations center (SOC) that provides customers with round-the-clock human and AI-led threat detection, analysis and mitigation services to protect against complex threats.
This article was originally published at Barracuda Blog.
Photo: Karel Bartik / Shutterstock
This post originally appeared on Smarter MSP.

