

A new malware loader, Tsundere Bot, is increasingly used by criminal Initial Access Brokers (IABs) to compromise corporate environments and pave the way for ransomware attacks. Recent public reporting links Tsundere Bot to ClickFix‑style phishing, malicious loaders delivered through user interaction, and follow‑on deployment of XWorm, information stealers, and ransomware.
What is the threat?
Tsundere Bot is an initial‑access malware loader used to establish persistence, collect system data, and download additional payloads. Attackers commonly deliver it through social‑engineering emails that urge users to “fix,” “repair,” or “update” something, leading them to run malicious files.
Common components in related campaigns
- Tsundere Bot: Primary loader; establishes C2 and downloads payloads
- XWorm: RAT used for remote control and post‑exploitation
- Ransomware payloads: Final stage for encryption/extortion
- ClickFix phishing: Delivers malicious code under the guise of “repair” actions
- Living‑off‑the‑land tools: Used for lateral movement and credential access
| Component / tool | Role in attack chain | Notes / configuration considerations |
| Tsundere Bot | Initial access loader / downloader | Installed via phishing/ClickFix flows; establishes C2 and loads payloads. |
| XWorm | Remote access trojan / post‑exploitation tool | Used after Tsundere Bot to maintain access and execute attacker commands. |
| Ransomware payloads | Final impact stage | Deployed once attackers have adequate access and privileges. |
| ClickFix‑style phishing | Initial delivery mechanism | Social engineering to convince users to run “fix” actions that are malicious. |
| Living‑off‑the‑land tools | Lateral movement / persistence / credential access | Native OS tools abused following initial Tsundere Bot infection. |
Note: Tsundere Bot is not a single vendor product, but part of a broader criminal toolkit used by multiple threat actors/IABs. Exposure depends on your email security posture, endpoint hardening, and user behavior.
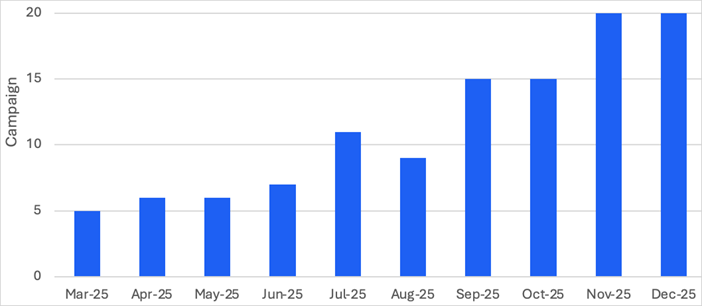
Number of TA584 campaigns
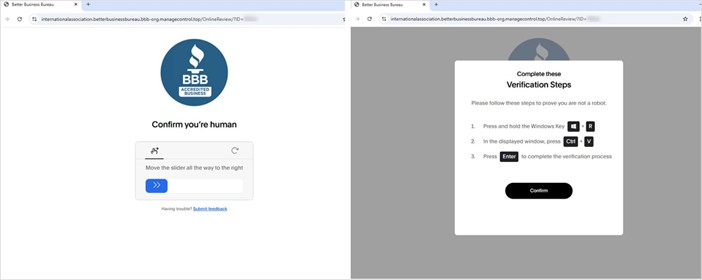
CAPTCHA (left) and ClickFix (right) pages
The command fetches and executes an obfuscated script, loads either XWorm or Tsundere Bot into memory, and redirects the browser to a benign site for deception.
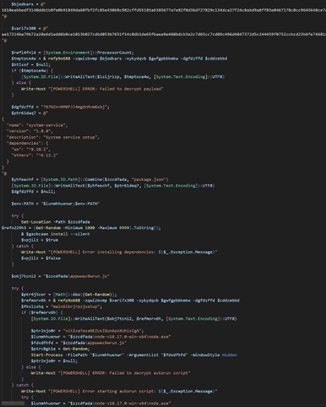
The PowerShell script
Why is it noteworthy?
- Growing IAB adoption: Increasingly used as a preferred initial‑access method.
- Modular and flexible: Easily loads RATs, stealers, or ransomware depending on the target.
- Highly effective social engineering: ClickFix lures mimic legitimate business workflows.
- Rapid attacker pivoting: Payloads and infrastructure can change quickly.
- High business impact: Risk includes data theft, BEC, ransomware encryption, and extortion.
What is the exposure or risk?
Organizations are at highest risk if users can open unknown attachments, run scripts, or click unsolicited “fix/update” links.
Key risks
- Endpoint compromise: Persistent foothold and outbound C2 channels
- Remote control: XWorm enables command execution, file transfer, and lateral movement
- Credential theft: Session cookies, browser credentials, VPN tokens
- Ransomware deployment: Encryption, data exfiltration, and prolonged downtime
- Resale of access: IABs may sell compromised access to multiple threat actors
What are the recommendations?
Barracuda recommends the following actions to mitigate this threat:
1. Email & content security
- Use advanced filtering, sandboxing, and URL rewriting
- Block scriptable attachments (HTA, VBS, JS, macro documents)
- Flag “fix/repair/update” themed lures
2. Endpoint hardening
- Ensure EDR/NGAV detects suspicious child processes and new persistence
- Enforce application allowlisting
- Keep OS, Office, browsers, and agents fully patched
3. Network controls
- Limit outbound traffic via deny‑by‑default egress
- Block malicious and newly registered domains
- Segment critical systems to reduce blast radius
4. Monitoring & hunting
Look for:
- Rare outbound domains shortly after email interactions
- Office or email clients spawning scripting engines
- New executables, run‑key changes, or scheduled tasks
5. Limit lateral movement
- Remove local admin rights
- Require MFA for VPN, email, and admin tools
- Restrict access from user networks to DCs, backup systems, and critical servers
6. User awareness
- Train on ClickFix‑style social engineering
- Use phishing simulations aligned to current campaign themes
7. If indicators are found
- Immediately isolate affected endpoints
- Preserve logs and suspicious files for analysis
- Reset credentials used on impacted systems
- Check for XWorm, data exfiltration, or ransomware staging
- Engage IR support if needed
References
For more in-depth information about the recommendations, please visit the following links:
- https://www.bleepingcomputer.com/news/security/initial-access-hackers-switch-to-tsundere-bot-for-ransomware-attacks/
- https://www.thaicert.or.th/en/2026/01/30/ta584-uses-tsundere-bot-and-xworm-in-clickfix-campaigns-increasing-ransomware-risk/
- Related public threat intelligence from security vendors and CERTs on initial‑access brokers, ClickFix phishing, XWorm, and ransomware loader ecosystems.
If you have any questions about this Cybersecurity Threat Advisory, don’t hesitate to get in touch with Barracuda Managed XDR’s Security Operations Center.
This post originally appeared on Smarter MSP.

