
 The U.S. Cybersecurity and Infrastructure Security Agency (CISA) confirmed active exploitation of a critical vulnerability in the self-hosted Git service Gogs, adding it to the Known Exploited Vulnerabilities (KEV) catalog. Federal Civilian Executive Branch agencies must apply mitigations or discontinue use of Gogs by February 2, 2026. Read the Cybersecurity Threat Advisory now to learn more and protect your clients’ environments.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) confirmed active exploitation of a critical vulnerability in the self-hosted Git service Gogs, adding it to the Known Exploited Vulnerabilities (KEV) catalog. Federal Civilian Executive Branch agencies must apply mitigations or discontinue use of Gogs by February 2, 2026. Read the Cybersecurity Threat Advisory now to learn more and protect your clients’ environments.
What is the threat?
CVE‑2025‑8110 is a path traversal and symlink bypass vulnerability in the Gogs PutContents API with a CVSS score of 8.7. It allows authenticated users to overwrite arbitrary files outside the intended repository directory by abusing symbolic links. Attackers typically target Git configuration files—such as sshCommand—to ultimately achieve remote code execution (RCE).
This weakness bypasses prior fixes for CVE‑2024‑55947, which failed to properly account for symbolic links, leaving path validation protections ineffective. Affected products and versions include:
- Gogs: All versions ≤ 0.13.3. Issue confirmed in published notice.
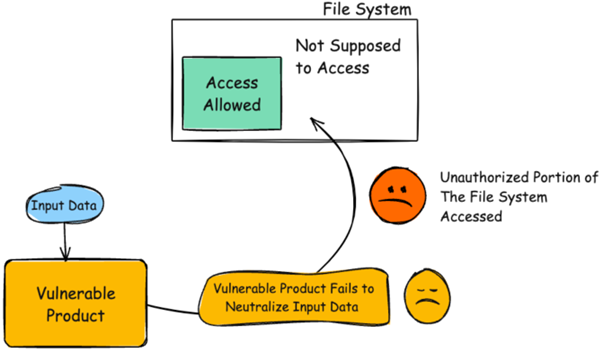
Why is it noteworthy?
- Active exploitation and federal deadline: CISA’s addition of the flaw to its KEV catalog triggers a mandatory requirement for federal agencies to patch or discontinue Gogs by February 2, 2026.
- Incomplete prior remediation: The issue remains exploitable due to earlier patches failing to properly address symlink handling, allowing attackers to bypass intended safeguards.
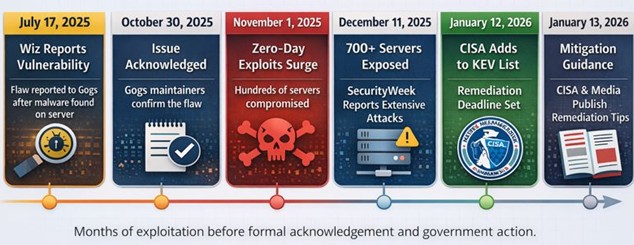
- Ongoing automated attacks: Evidence indicates at least two waves of exploitation since November 2025, likely driven by scripted or automated campaigns.
What is the exposure or risk?
The exploitation of CVE‑2025‑8110 in Gogs creates several major security and operational risks:
- Remote Code Execution (RCE): Attackers can overwrite critical config files and run arbitrary commands on the host system.
- Persistent Access: Compromised servers may be used to deploy malware, plant backdoors, or modify SSH keys and Git hooks for long‑term control.
- Credential Theft & Lateral Movement: Stolen credentials or tokens enable attackers to move deeper into developer environments and adjacent systems.
- Supply Chain Risk: Attackers can poison repositories, tamper with code, or compromise CI/CD pipelines and downstream software.
- Data Exposure: Private repositories, source code, and sensitive configuration secrets may be stolen.
- Operational Disruption: Exploitation can corrupt repositories, cause outages, and force time‑consuming rebuilds.
- Compliance Impact: Breaches involving source code or customer data may trigger regulatory or contractual reporting obligations.
- Large Attack Surface: With 1,400+ internet‑facing servers and over 700 known compromises, automated mass exploitation is highly likely.
What are the recommendations?
Barracuda recommends the following actions to limit the impact of CVE-2025-8110:
- Apply updates containing symlink-aware path validation (fixes available post-CVE disclosure). Monitor Gogs main branch on GitHub for release status.
- Disable open registration unless absolutely necessary and Restrict access via VPN or IP allowlists.
- Search for suspicious repository names (random 8-character strings), unusual PutContents API calls, and changes to .git/config.
- Disconnect, collect forensic data, rotate SSH keys, review commit history, and rebuild from clean sources for compromised systems.
- Enable audit logging of file-write APIs. Set SIEM alerts on unexpected .git/config modifications or symlink creation.
- Ensure compliance; FCEB agencies must finalize mitigation by February 2, 2026 under CISA’s KEV mandate.
References
For more in-depth information about the recommendations, please visit the following links:
- BleepingComputer – “CISA orders feds to patch Gogs RCE flaw exploited in zero‑day attacks” (January 12, 2026)
- Infosecurity Magazine – “CISA Flags Actively Exploited Gogs Vulnerability with No Patch” (January 13, 2026)
- The Register – “Federal agencies told to fix or ditch Gogs as exploited zero‑day lands on CISA hit list”
- CyberPress – “CISA Warns of Actively Exploited Gogs Path Traversal Vulnerability” (January 13, 2026)
- SecurityWeek – “Unpatched Gogs Zero‑Day Exploited for Months” (December 11, 2025)
- TechRadar Pro – “US government told to patch high‑severity Gogs security issue or face attack” (January 13, 2026)
If you have any questions about this Cybersecurity Threat Advisory, don’t hesitate to get in touch with Barracuda Managed XDR’s Security Operations Center.
This post originally appeared on Smarter MSP.

