Security researchers have uncovered a new attack method known as “FileFix,” which exploits Windows File Explorer to execute stealthy PowerShell commands. By abusing legitimate Windows functionality, attackers can run malicious code while evading traditional security controls. Read this Cybersecurity Threat Advisory to understand the risks and how to defend your organization.
Security researchers have uncovered a new attack method known as “FileFix,” which exploits Windows File Explorer to execute stealthy PowerShell commands. By abusing legitimate Windows functionality, attackers can run malicious code while evading traditional security controls. Read this Cybersecurity Threat Advisory to understand the risks and how to defend your organization.
What is the threat?
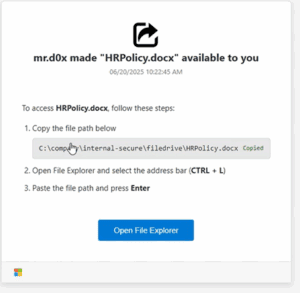
The FileFix attack is a social engineering technique that exploits Windows File Explorer’s address bar functionality to initiate PowerShell commands without user awareness. When a victim interacts with a malicious website, the attack works by:
- Automatically copying a malicious PowerShell command to the victim’s clipboard.
- Presenting what appears to be a legitimate file path in Windows File Explorer.

- Executing the PowerShell command when the user attempts to navigate to the fake file path.

FileFix poses a unique threat because it executes malicious actions silently, without triggering user suspicion or traditional security alerts. The attack can deliver various payloads, including ransomware, information stealers, or remote access trojans.
Why is this noteworthy?
The FileFix attack is noteworthy for several reasons including:
- Evasion of security controls: Instead of exploiting a vulnerability, the attack abuses built-in Windows behavior to sidestep conventional defenses.
- No CVE assignment: Unlike traditional vulnerabilities, this attack technique doesn’t have a CVE identifier because it’s not exploiting a software bug but rather abusing legitimate functionality in an unexpected way through an unsuspecting user.
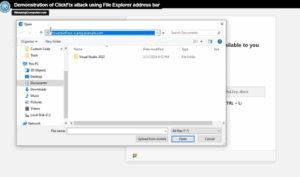
- Evolution of attack techniques: FileFix is an evolution of the previously identified “ClickFix” attack, showing how threat actors continuously refine their methods.
- Minimal user interaction: The attack runs silently and requires little user input, making it highly effective for social engineering campaigns without raising suspicion.
- Widespread adoption: According to recent reports, the Interlock ransomware group has already adopted this technique to deliver malware, indicating its effectiveness and rapid adoption by threat actors.
What is the exposure or risk?
Any Windows user with access to File Explorer may be at risk, as this attack exploits legitimate Windows functionality, making it difficult to detect. It has the potential for widespread impact, particularly through phishing campaigns or compromised websites.
A variant of this technique has also emerged on Linux. In this case, visiting a malicious website can automatically copy a shell command to the user’s clipboard. The user is then prompted to open a Run dialog and execute the command—unknowingly triggering unauthorized PowerShell execution. This can lead to data theft, system compromise, ransomware deployment, or serve as an initial foothold for more advanced attacks.
What are the recommendations?
Barracuda recommends organizations implement the following measures to protect against FileFix attacks:
- Implement PowerShell Script Block Logging, Module Logging, and Constrained Language Mode to detect and prevent malicious PowerShell execution.
- Use application control solutions to restrict PowerShell execution to only authorized scripts and commands.
- Deploy advanced endpoint protection to detect and block suspicious PowerShell activity, even when executed through legitimate Windows components.
- Implement comprehensive logging and monitoring to detect unusual PowerShell commands or File Explorer behavior.
- Implementing policies to restrict PowerShell execution for standard users who don’t require it for their daily tasks.
How can Barracuda protect you against this threat?
Barracuda offers several solutions that can help protect against FileFix attacks:
- Barracuda Managed XDR: Provides 24/7 monitoring and threat detection capabilities to identify suspicious PowerShell activities, even when executed through legitimate Windows components. The service includes expert security analysts who can help detect and respond to exploitation attempts.
- Barracuda Email Protection: Helps prevent phishing emails that might contain links to websites deploying FileFix attacks, with advanced threat protection capabilities that can identify and block malicious URLs.
- Barracuda SecureEdge Access: Blocks access to malicious websites that might attempt to deploy FileFix attacks, providing an additional layer of protection for users browsing the web.
- Barracuda CloudGen Firewall: Offers advanced network protection features that can help detect and block suspicious network traffic associated with command and control communications following a successful FileFix attack.
References
For more in-depth information about the recommendations, please visit the following links:
- https://www.bleepingcomputer.com/news/security/filefix-attack-weaponizes-windows-file-explorer-for-stealthy-powershell-commands/
- https://www.bleepingcomputer.com/news/security/interlock-ransomware-adopts-filefix-method-to-deliver-malware/
If you have any questions about this Cybersecurity Threat Advisory, don’t hesitate to get in touch with Barracuda Managed XDR’s Security Operations Center.
This post originally appeared on Smarter MSP.